- Technical difficulty: ★☆☆☆☆
Asymmetric cryptography is very useful for a variety of systems. With asymmetric cryptography, you can:
- encrypt contents of a message in a way that only the intended receiver can open it
- verify the identity of certain people or machines
- digitally sign data to make sure it is really coming from you.
How it works
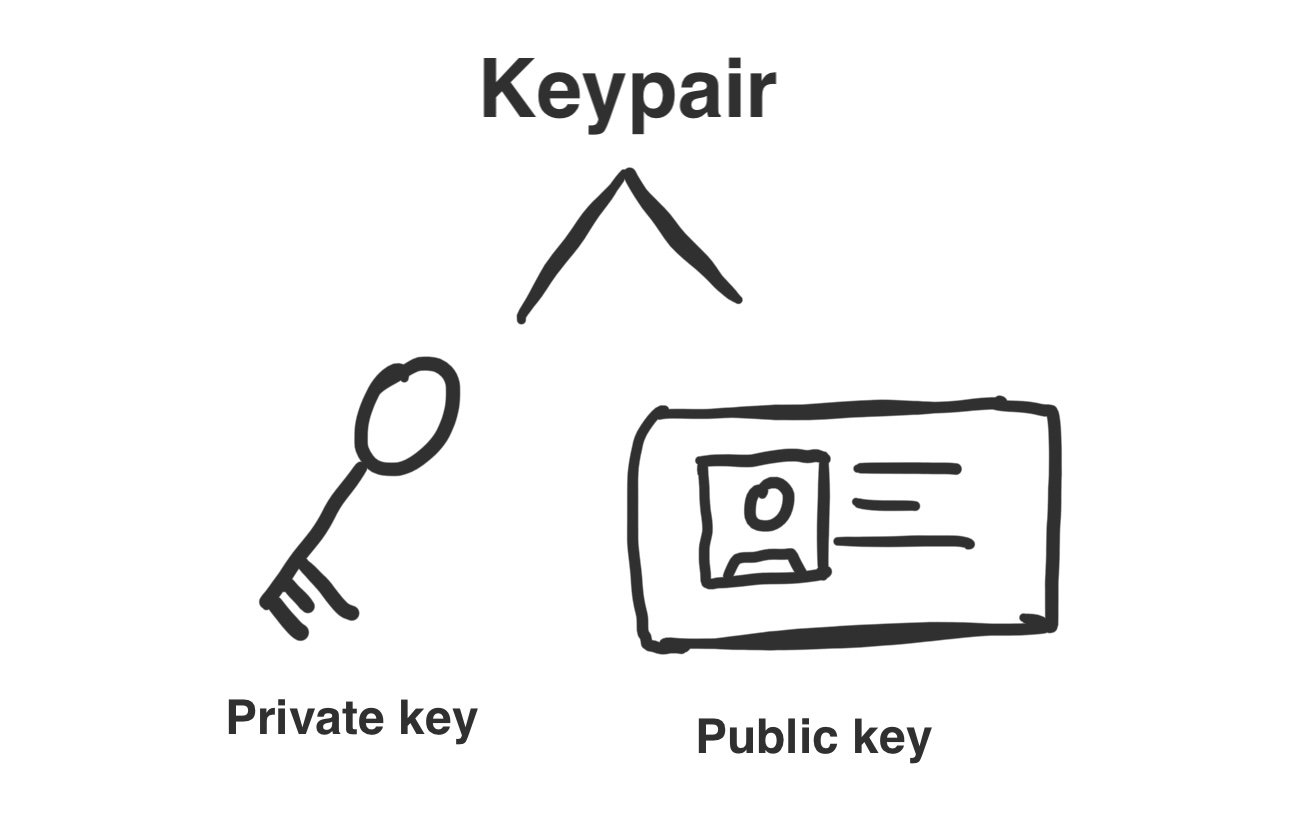
Asymmetric cryptography works by generating and using key-pairs. Key-pairs consist of two keys:
- The public key: This is your identity (Imagine it to be some sort of ID). You can share this with anyone
- The private key: This is a private key that you NEVER share with anyone, as the name implies. This key allows you to prove you are the owner of your public key. In other words, that you are who you claim to be.
Let's imagine Alice wants to digitally sign a message to Bob to prove it is really coming from her. Here is how it works:
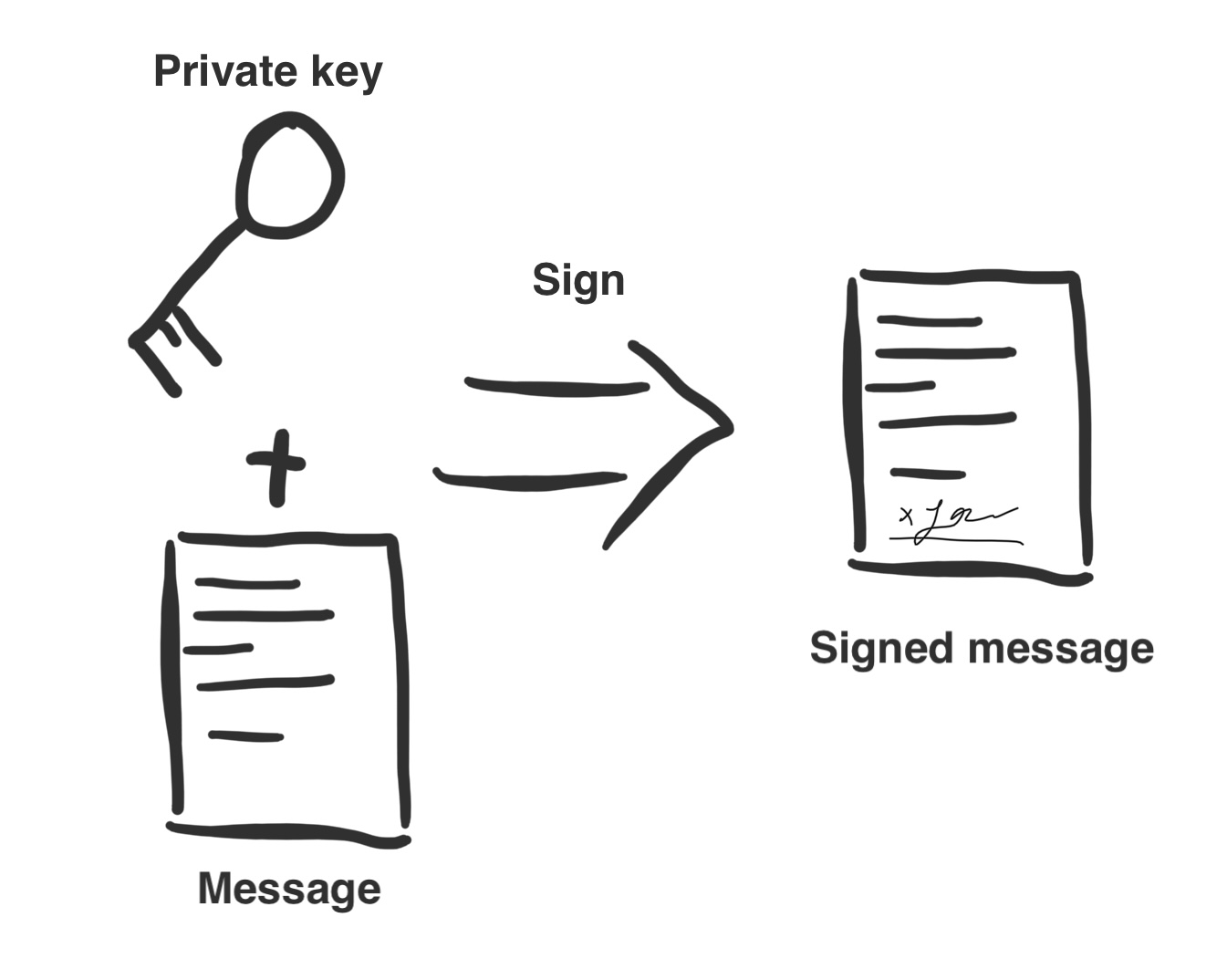
- Alice generates a key-pair. She keeps the private key to herself and shares the public key with Bob and everyone else.
- Alice uses her private key to sign the message. This creates a signature that is unique to her private key and the message.
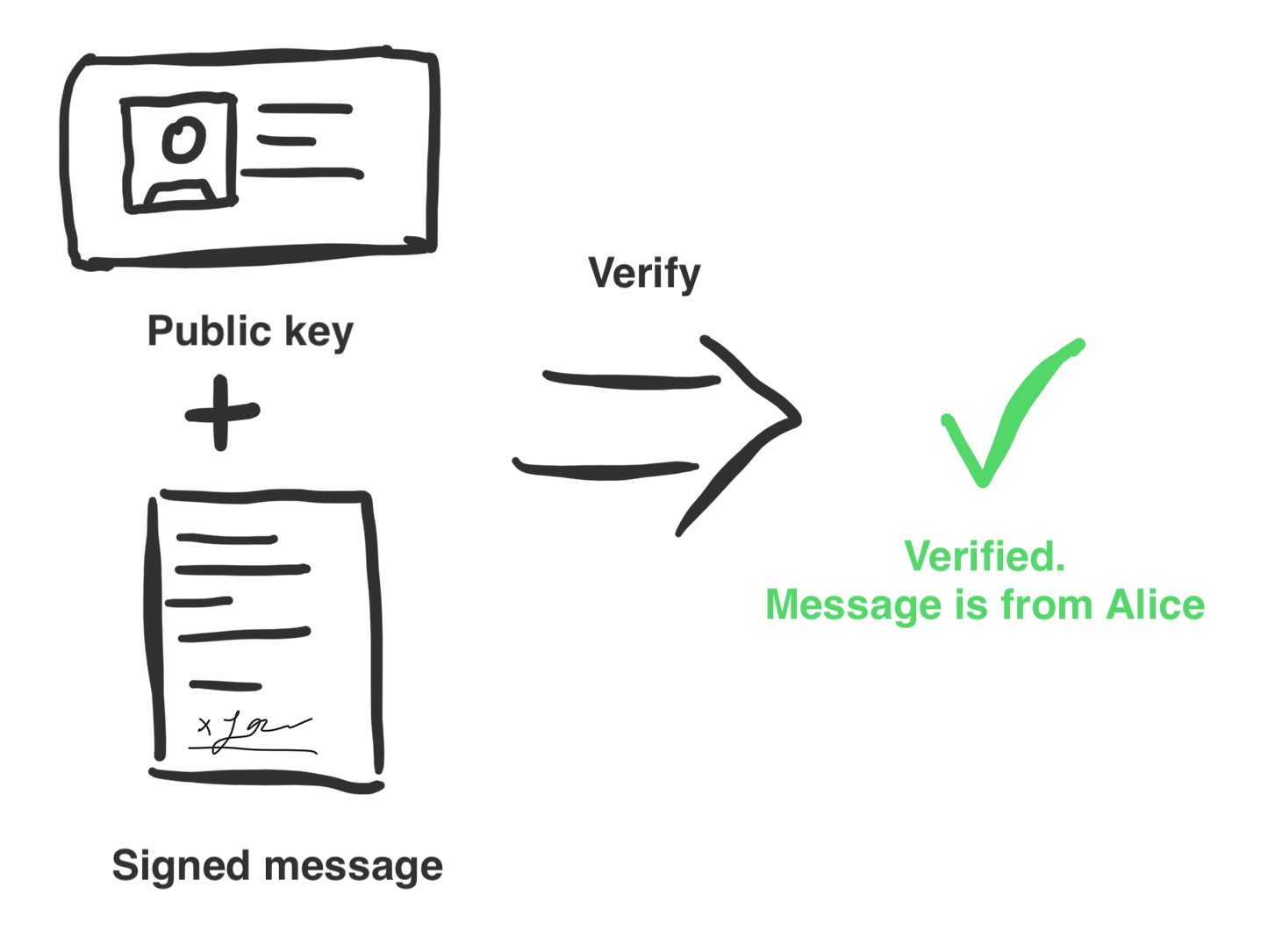
- Alice sends the signed message to Bob. Bob can use Alice's public key to verify that the message was really signed by Alice. If the signature is valid, Bob can be sure that the message was really signed by Alice.
Real use case examples
- SSH access: SSH (Secure shell) can use these keys to prove you are allowed access to a certain computer, without having to send your password.
- Digitally signing software packages: Software publishers often use GPG/PGP to digitally sign an app and prove that a given app package is coming from them (and not a malicious impersonator)
- Bitcoin: Bitcoin uses asymmetric cryptography to prove a financial transaction is being performed by the owner of a specific wallet
- Nostr: Nostr is a novel social network protocol that uses asymmetric cryptography to verify that social media posts were actually posted by the author, without requiring an authority or a centralized server
Further learning
This guide is a very high-level overview of asymmetric cryptography. If you want to learn more, here are some resources:

